

| For Unix, NT/Win95, OS/2, VAX VMS and Amiga |
| Latest Release: |

|
| Initial Release: |

|
Please check this section periodically to see what have been changed or added.
It is reported that the Count 2.3 runs on the following platforms, hopefully 2.4 will be portable as well.
Operating System First reported by AIX 3.2.5 robtuck@coeibm.rutgers.edu Amiga albertv@spinnewiel.xs4all.n (ported by) AU/X jussi.haro@tothepoint.fi BSDI chris@technonet.com DEC OSF1 ma_muquit@fccc.edu DG/UX irrigacion@planet.losandes.com.ar DomainOS 10.4.1 (on Apollo Workstns) philippe.hubaut@etud.insa-tlse.fr FreeBSD 2.1.5 tomcat@1lo.lublin.pl HP-UX takao.tsukiyama@tokyo.tohmatsu.co.jp Linux ashley@photocraftlab.com NetBSD makoto@komekome.bay.prug.or.jp NEXTSTEP 3.3,3.2,4.0 for Mach
(Motorola,Intel)jk@exnext.com NT 3.51 (intel) ma_muquit@fccc.edu NT 4.0 with IIS 2.0 srakhtar@ix.netcom.com SunOS 4.1.x ma_muquit@fccc.edu Solaris 2.x ma_muquit@fccc.edu SCO yuqiao@UDel.Edu SGI ma_muquit@fccc.edu SINIX 5.4 (SVR4, MX500I by Siemens Richard.Bothe@mch.sni.de ULTRIX 4.3 mbarria@ing.puc.cl UnixWare 2/2.03 ebh@fpk.hp.com
ivanlan@tzuk-te.callware.comVMS phil@pottsoft.demon.co.uk (ported by) Win95 null@dent.showa-u.ac.jp
OS/2 dshields@direct.ca (2.3) [ported by)
This is a CGI program to keep record of the raw hits of a web page. It generates a GIF image of the number of hits and returns to the browser as an in-lined image. The program also has a run-time option not to show the digit images, this way the hits can be kept without displaying it. The hits can be be monitored without incrementing from a separate page as well. Almost all of the features are run-time options. This program started as a fun to play with CGI programming but due to enormous interest, feature request, input from thousands of you, it has turned in to the most configurable counter on the whole World Wide Web.The program is distributed as a gzip'd tar archive. If you do not have gzip/gunzip, it is available a tar archive at: prep.ai.mit.edu. The URL is:
ftp://prep.ai.mit.edu/pub/gnu/gzip-1.2.4.tar
|
Before going to the configuration procedure, please browse through the default directory structure below. It will help you answering questions of the configuration script. You can change the name of the directories as you please, but keep the directory structure same, it will make your life much easier. You do not have to create any of these directories, they will be created for you by the Count-install program. Only thing you probably have to create are the individual datafiles (keep reading).
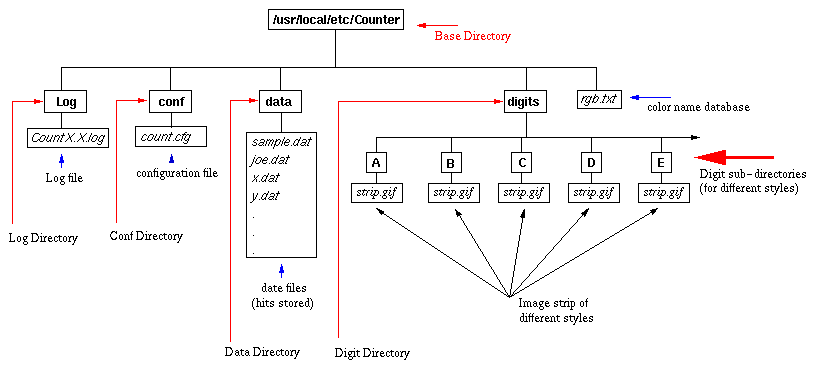
Base Directory is the directory where all the sub-directories and the files related to counter reside.
Log Directory is the directory which holds the counter Log file. Counter error messages or if someone tries to access your counter remotely, warning message regarding this is written to this file.
conf directory holds the configuration file for the counter. configuration file holds information in 4 blocks. Each block resides between a left and right curly brace. This file is created by the program Gen-conf and can be hand crafted later. After creating the file, please read the comments in the file.
data directory holds all the datafiles for the counter. The datafiles stores the access counts of web pages. Each page must have a separate datafile. The datafile is specified at run-time. You will know about it later.
digits directory holds sub-directories with various styles of GIF digits. For example, A sub-directory holds the green led digits. The sub-directories have GIF digit files named zero.gif, one.gif...nine.gif. you will know about it later.
rgb.txt file is used to convert a color name (for example, cyan) to the appropriate red, green and blue color component. This file came from X consortium and supplied with the distribution. You will know about the file later.
The digits used in this program can be individual GIF files or all the digits can be in a single image strip. This gives flexibility of using digits of your choice. In case of individual digit images, they are named as zero.gif, one.gif,.... nine.gif. In case of image strip, the strip is named as strip.gif. At run-time, simply the directory of the images is specified to use a different style. Therefore, a single program can display digits of various styles. Here are the supplied digit styles. I will not supply individual digit images anymore. All the styles of digits are supplied as a single image strip. Note the order of the digits (you will know about it later).
Style A 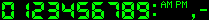
designed by the author
(digits/A/strip.gif)Style B 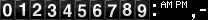
Borrowed from HTML-access counter. (digits/B/strip.gif) Style C 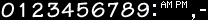
designed by benjamin@pop3.oro.net
(digits/C/strip.gif)Style D 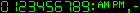
designed by the author
(digits/D/strip.gif)Style E 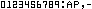
desined by the author
(digits/E/strip.gif)A suggested use of style E is to make the white color transparent (you will know about transparency later).
For a huge collection of GIF digits, check out the Digit Mania page.
Some other sites:
This program will work with any digits from the Digit Mania page. To use those digits, create subdirectories say, F,G, H etc. inside the digits directory and rename the images to zero.gif, one.gif..nine.gif. I suggest create an image strip out of these digits and use it instead of using individual images.
Before using these digits, please read the sections How to use other styles of digits and How to create an image strip.
The source code for this program is distributed as a gzip compressed tar archive.If you do not have gzip/gunzip, it's available at: prep.ai.mit.edu.
If you do not have gzip/gunzip and tar for NT, they are floating around on the net. Please do not ask me to supply a zipped version for the source distribution.
Download source code archive (2.4) (gzipped, tarred)
[Latest Version]Please visit the page for NT binary
Download source+binary archive (2.3) for OS/2 (pkzipped)
This port of Count 2.3 is done by Doug Shields ( dshields@direct.ca).
Please read the file readme.os2 for details.
Go to VMS port page
The port of Version 2.3 to VMS is done by Phil OttewellA port to Amiga is done by Bert Vortman He added the source and binary archive to Aminet. Here'r the links of the Amiga port:
ftp://ftp.uni-paderborn.de/pub/aminet/comm/www/wwwcount2.3bin.lha ftp://ftp.uni-paderborn.de/pub/aminet/comm/www/wwwcount2.3src.lha or http://ftp.wustl.edu/~aminet/dirs/aminet/comm/www/wwwcount2.3bin.lha http://ftp.wustl.edu/~aminet/dirs/aminet/comm/www/wwwcount2.3src.lhaThere are several other Aminet servers who are mirrors of the wuarchive.wustl.edu site.
The file wwwcount2.3.tar.gz is a gzip'ed tar file. To extract the distribution, at the shell prompt, type:
gunzip < wwwcount2.3.tar.gz | tar xvf - cd wwwcount2.3The program will compile with ANSI or non-ANSI C compiler.
In the current release of the counter, there should not be any need for hand editing any files. Several configuration scripts are supplied to automate the whole process. I am giving a little description about the scripts just may be you are curious:Count-config
script to generate the header file config.h, a variable template file for install program.configure
script to generate correct Makefiles for any Unix system.Gen-conf
script to generate the configuration file.Count-install
script to install the Count binary Count.cgi, digit images, configuration file and the rgb color name database to the correct places.Now at the shell prompt (shell prompt is where you type ls, read your mails etc.), type the following commands in the described order and press Return key:
Step 1
./Count-configThe script will ask questions with brief description. Answer them. Look at the directory structure image to better understand the questions.
Look at a sample sessionStep 2
./configureThe script will not ask any questions, but you will see the informational messages about your system. It will create the Makefiles (Makefile, combine/Makefile and utils/Makefile) for your system.
Look at a sample sessionStep 3
make clean
makeCompilation will start if the previous two scripts completed successfully. It will take some time. If compilation succeeds, go to the next step.Step 4
./Gen-confThis script will ask you questions about your system. Answer them. This process will create the configuration file for the counter.
Look at a sample sessionStep 5
./Count-installThis is the final step. This scripts will install the necessary things for the counter in your system. You will need root access if you are installing it an area where root access is needed. This program will ask you some questions.If you finished all the above steps successfully, you are ready to test the counter.
You do not need to compile the program for NT in order to use it. A compiled version is already supplied. I compiled the program on NT 3.51 (intel) with MS Visual C++ 4.0. The makefiles supplied are for MS Visual C++ 4.0 as well. If you use some other kind of compiler, you are on your own.Assuming you already downloaded and extracted the sources from the archive. Open a command shell window and perform the following steps:
1. cd wwwcount2.3 2. Edit the file configNT.h and see if you need to change anything. 3. cd combine 4. nmake -f makefile.wnt 5. cd .. 6. nmake -f makefile.wntThe above procedure will create the executable Count.exe. Copy the file Count.exe to your cgi-bin or scripts directory or where ever you keep the CGI programs. Open the File Manager and copy or move the directory wcount to C drive (if you edited the file configNT.h and changed the location, copy it there). Read the section How to call the program?.If you want to create the program mkstrip.exe, do:
1. cd utils 2. nmake -f makefile.wnt 3. Copy or move the file mkstrip.exe to somewhere in your path.
A shell script is provided to test out the various features of counter.
To test the program, at the shell prompt, type:
cd tests
./testcount-sh
The test program executes the Counter program Count.cgi and creates a html
file and a gif file. The html file is then loaded to the "netscape" browser.
THe tests will not work with with any other browser.
You can refer to the program from web page like this:<img src="/cgi-bin/Count.cgi?df=sample.dat" align=absmiddle>
The string between ? and " is called the QUERY_STRING. Make sure there is no newlines in the <img src= line and no space in the QUERY_STRING. Here in, df=sample.dat, df means datafile and sample.dat is the counter datafile. The counter stores the hits in this file. This datafile is supplied. If you configured the counter to allow automatic datafile creation (look at count.cfg file), you can specify a datafile with df like df=count.dat. The file count.dat will be created for you if the permission to the data directory is correct.
If you configured not to allow automatic datafile creation (good thing), you have to create this file in the data directory. cd to the data directory and type:
echo 1 > count.datThe counter program has lots of options, you can make it work and look the way you desire. In the query string, you can use the options described in the table below. The options can be separated by a | or a &. You can use either one or combination of both. Here is an example:
<img src="/cgi-bin/Count.cgi?ft=T&frgb=gold|df=sample.dat" align=absmiddle>The options can be in any order and not case sensitive.
Anyway, look at this Example Page you will get the picture.
| Parameter | Name | Description | Default |
|---|---|---|---|
|
cache=B expires=X |
These parameters can be used to change the image caching behavior of certain web browsers. |
The boolean value of cache hints the browser whether to
cache the image or not.
The integer value of expires specifies the cache
expiration duration time in seconds.
If you specify cache=F, the browser
will be hinted to cache the image for the amount of seconds
specified with expires parameter. if cache=F and expires=0, then
the browser should not cache the image, that is whenever you
come back to the page, the counter or clock will be refreshed.
Use this feature with discretion as it may increase load on your
system. The expires parameter is meaningless without
cache=F, that means, ff cache=T is specified, expires
parameter is ignored and the counter will not generate any
HTTP Expires header. This is the default behavior.
The valid values for the boolean parameter cache is Y,N,F,T 1 or 0.
The valid integer range of the expires parameter is between 0
and 604800 (7 days).
Note, these parameters will work with browser supports the HTTP Expires header as specified in HTTP specification. By default, most web browsers caches the image got from the counter. That means, if someone visits your page and comes back after a while, the counter or clock does not get refreshed. |
cache=T expires=0
|
| display=X | Specifies what to display. | A valid string can be specified with display= parameter to display counter, clock or date. The valid value for the string parameter X is counter, clock or date For counter, this parameter is not need as counter is the default display type. | display=counter |
| timezone=X | Display time/date of the specified timezone. |
The parameter timezone= is only significant with
display=clock or display=date. Use this parameter
if you want to display time or date of another timezone.
The timezone must be specified with a negative or positive
four digit offset from GMT, for example: timezone=GMT-0500 or
timezone=GMT+0000 or timezone=GMT+0530.
The routine to display time of various timezones are written in a
generic way. Therefore, the unix machines will not be aware of
daylight saving time because of the way the routine is written. For
example, if daylight saving time is on, to display time of NY, the
timezone will be timezone=GMT-0500 instead of
timezone=GMT-0400. If the clock displays your local time wrong, specify your timezone with that parameter in order to display the correct time. |
None. |
|
tformat=X
|
Time format in 12 or 24 hour. | This parameter can be used to display time in 12 or 24 hour format. The valid values for the parameter X is 12 or 24. | tformat=12 |
| dformat=X | Specifies date format. | This parameter is only significant with display=date. The valid value for the string parameter X is any combination of MMDDYY (Month-Day-Year). For example, dformat=ddmmyy, dformat=YYMMDD. | dformat=MMDDYY |
| istrip=B | Use of image strip On/Off | The boolean value of istrip specifies whether to use image strip or not. If you specify istrip=F, the program will look for the individual digit image files in the digits/style directory. The valid values for the Boolean parameter istrip are Y, N, T, F, 1 or 0. | istrip=T |
| ft=X | Frame Thickness | You can wrap the counter in an ornamental frame of X pixels thick. Use 0 for no frame. Values over 5 make a nice 3-D effect. | ft=6 |
|
frgb=R;G;B or frgb=RRGGBB (in hex) |
Frame Color |
Specifies the color of the frame in RGB (red/green/blue)
format. Each color component, R, G, and B is specified as a
value between 0 and 256. If you use ft= without a frgb=
param, the default color is used.
If you specify a frgb= without a ft=, then the frame thickness defaults to 5. All the examples show ft=5. The color can be specified as hex string or a name. Do not use a # before the hex string as Netscape. For example, if you want to specify white in hex, use frgb=ffffff. You also can use a color name (e.g. frgb=blue) if the counter configured to do so (look at the cfg file). Look at the color name mapping database for some hints about color name database. |
frgb=100;139;216
or frgb=648bd8 |
| tr=B | Transparency On/Off | You can specify if your counter image will have a transparent color with the Boolean B. So tr=Y means there will be a transparent color. It does not matter if the GIF files used for the digits are "transparent"; you must specify explicitly which color to make transparent. If you specify a trgb=, then you do not need to specify tr=Y. If you specify tr=Y and do not specify trgb=, then the default color black will be transparent. The valid values for B are Y, N, T, F, 1, or 0. |
tr=F
No Transparency |
| md=X | Max Digits | Defines maximum number of digits to display. Any value between 5 and 10 inclusive are permitted. Padding with leading zeros is automatically done for you; longer counts are truncated to the given X. |
md=6
Without padding |
| pad=B | Padding with 0's | Turn padding on/off in conjunction with md= setting. Valid values for the Boolean parameter B are Y, N, T, F, 1, or 0. |
pad=N
Without specification of a md=value
pad=Y |
| dd=A | Digit Directory | Denotes directory of a specific styles of digits. Four styles of digits are supplied. They are kept at the directories A,B,C and D respectively. Visit the digit mania page for other styles of digits. |
dd=A
My green led digits |
| image=gif_file | Display this GIF file | You can display any GIF image specified with this parameter. The location of this file is determined by the dd= parameter, that no path in the GIF file is allowed. All attributes of the counter apply to the image. | None |
| comma=B | Display comma after every 3rd digit from right. | The boolean value of parameter comma specifies whether to display comma after every 3rd digit from right. If you use this parameter as true, the left padding with zeros will be turned off. | comma=F |
|
srgb=R;G;B or srgb=RRGGBB (in hex) prgb=R;G;B or prgb=RRGGBB (in hex) |
Change a color of the image to a target color on the fly. | Any one color of the image can be changed to a different color on the fly. srgb stands for source color, that is the color to change. prgb stands for pen color, that is the target color. The values for srgb and prgb can be colon separated color components (e.g, srgb=255;0;0), a hex value (e.g. srgb=ff0000) or a color name (e.g. srgb=red). The color name can be used if you configured the counter to do so (look at the cfg file). |
srgb=00ff00 (0;255;0 green)
prgb=00ffff With chcolor=T |
| chcolor=B | Change a color of the image. | This parameter is usually used to change the default green color to cyan. That is if you specify chcolor=T, and you want to change green to cyan, then you do not need to specify srgb and prgb parameters. 1x1 GIF is displayed. The valid values for the Boolean parameter B are Y, N, T, F, 1, or 0 | chcolor=F |
| st=X | Start Count | This parameter is used to set the initial value of the counter to some number X. This is only valid if you decided to allow automatic datafile creation. It is a bad practice to allow automatic datafile creation, however it makes site maintaining easier. The automatic datafile creation option is specified in configuration file and can be changed at run time. Note that this parameter has no effect if the datafile already exists. If you want to change the counter value in a existing datafile, hand edit the file. The minimum value for st is 1. |
st=1 Count starts at 1 |
| sh=B | Show digits |
Used to turn display of digits on or off according to the
Boolean B. When sh=T, counter will be displayed and incremented,
this is the default behavior.
If sh=F no digits will show, but the counter will still increment; instead of digits a transparent 1x1 GIF is displayed. The valid values for the Boolean parameter B are Y, N, T, F, 1, or 0 |
sh=Y |
| df=data_file | Datafile to store count |
Specifies the name of the file for storing the count in. The
file must be allocated to you as was mentioned in the
"Authorizations" section above. You can use df=random
to display a random number.
One special use of the parameter is df=RANDOM. This returns a random number using the fractional portion of the host's time of day clock as a seed for the generator. Unlike all other WWWcounter parameters, the file name provided is case-sensitive, except for the value random. Or Random, or rANDOM, etc. |
df=random
if no datafile is specified |
| incr=B | Increment Count |
Makes it possible to display the current count without
incrementing the count. This can be used to examine the count
for reporting or other purposes without adding to the count.
Valid values for the Boolean parameter B are Y, N, T, F, 1, or 0.
|
incr=T
Increment the counter on each invocation |
| lit=X | Display literal | Makes it possible to display a given, predetermined string. The valid values for the string X are digits, a,p,: and - | None |
| negate=B | Negate the color | Makes it possible to negate the color of the counter digits. Note that the Frame is exempted from negating. Valid values for the Boolean parameter B are Y, N, T, F, 1, or 0. |
negate=F
Do not negate |
| degrees=X | Rotate X degrees | Makes it possible to rotate the counter image X degree. The possible values of X is 90, 180, 270 and 360. Note 360 is meaningless as the counter will come back to the original 0 degree. |
degrees=270
With rotate=Y and without degrees=X rotate 270 degrees clockwise |
| rotate=B | Rotate On/Off | The Boolean value B turns on or off rotating. If you use degrees= setting, rotate is not needed. Valid values for the Boolean parameter B are Y, N, T, F, 1, or 0. |
rotate=F
Do not rotate |
There are several sites including Digit Mania which maintains a array of collection of GIF digits which can be used with the counter. The counter program can use these digits in 2 ways.The section How to create an image strip describes how to create an image strip from individual digit images. If you like to use the individual digits instead, you must use the option istrip=F when you call the counter from web page, because by default istrip=T.
- use a individual digit image for each digit, for example, zero.gif, one.gif...nine.gif. These digit images reside in the digits/style directory. If you like to use the counter for clock, 3 additional digit images are required, e.g., colon.gif, am.gif and pm.gif. If you want to use comma in your counter digits, another image is required, e.g., comma.gif. If you want to use the counter to display date, one more image is required, e.g., dash.gif. If you collect digits from external source, do not forget to rename the images to zero.gif, one.gif, two.gif, ... nine.gif, colon.gif, am.gif, pm.gif, comma.gif and dash.gif
- use a single image strip for digits. This is the default behavior, that is the counter program looks for a image file called strip.gif in digits/style directory by default. Using an image strip is much more efficient than using individual digits, because
- the size of an image strip is almost always less than the combined size of individual images.
- Disk i/o is significantly reduced, because only one file needs to be opened instead of many.
If you have individual digit images, you can create an image strip out of them. Image strip reduces disk i/o significantly, because the counter will need to read only one image instead of many and the size of the image in most cases will be less than the combined size of the individual images.A program called mkstrip is supplied to create the image strip from individual digit images. Another program called extdgts is supplied to extract individual GIF images from the strip.gif (made with mkstrip). extdgts is there to help you out if you need to extract the digit images for some reason.
To compile the programs, go to the
utilsdirectory and at the shell prompt, type:makePlease note, these programs require the GIF image combining library. Therefore, compile them after compiling the counter. copy mkstrip and extdgts somewhere in your path.Now, go to the directory where all the individual digit images are and type:
mkstrip zero.gif one.gif two.gif .... nine.gif colon.gif am.gif pm.gif > strip.gifNote, the file names are not important but the order is very important. For example, the file names may be 0x.gif, 1x.gif etc.Create a directory say F inside the digits directory and copy or move the file strip.gif to F. You can use this strip with dd=F.
The above strip can be used for counter and clock but not date. It also can NOT be used if you want to display comma. If you want to use date and comma, you must have the image for comma and dash. For example, the strip of digit style A is created with the command:
mkstrip zero.gif one.gif ... nine.gif colon.gif am.gif pm.gif comma.gif \ dash.gif > strip.gifPlease note the order of the images used in arguments carefully. The program mkstrip puts the necessary information in the GIF comment extension about the strip. The counter program parses the comment extension to determine the width of the individual digits in the strip. Therefore, the strip can have digit segments of variable width.For example, the comment of the image strip of digit style A is:
15:0:15:30:45:60:75:90:105:120:135:150:165:180:195:210:225The leftmost integer 15 indicates there are 15 individual digits in the image and the next colon separated pairs are the location of left and right side of the segment of the individual images from the leftmost edge. If you look carefully you will see that the individual segment of the strip is 15 pixel wide. The height is determined by reading the image. If you use the program mkstrip, you do not need to know anything about the comment, it will be created correctly for you. It is mentioned here because it is possible you obtained a strip from somewhere and you want to add the comment to the image.
The configuration file count.cfg is a text file. Any line starts with # is considered a comment and everything after the # is ignored. The config file for Count 2.4 has 5 blocks. Each block starts with a "{" and ends with a "}" each on a separate line. The following is a sample count.cfg file.####### # configuration file for Count 2.4 # Edit by hand, if you need to add something ############################################## #### # BLOCK 1 # Allow automatic datafile creation or not # it's a required block. 1 means allow, 0 means do not allow. #### { 0 } ### # BLOCK 2 # run the program in strict mode or not. # it's a required block. 1 means strict, 0 means not strict. ### { 1 } #### # BLOCK 3 # Allow to use RGB color database. 1 means allow, 0 means don't # convenient to use because colorname e.g., red, gold etc can # be used instead of rgb components of the color, however it's # very inefficient to lookup. #### { 1 } #### # BLOCK 4 # Ignore count block, you might want to ignore the local sites. # If you do not want to ignore any hosts from # counting, just put { on one line and } on the next line but make sure # the braces exist! # It's a required block. ###### # netmasks can be used to ignore a entire network or a specific # range of hosts in the network. Read the counter documentation to # know about netmasks. #192.160.166.0 255.255.255.0 { 131.249.* } #### # BLOCK 5 # Auth block # All possible names and IP addresses by which your host can be referred. # These hosts can access the counter remotely or locally. Host running # the http server must exist here. ## { test.counter.com www.fccc.edu* warm 192.160.166.1 www 193* }The config file is parsed each time the Count.cgi gets accessed. Therefore, smaller the file, better the performance. If you have thousands of entries in block 4 or block 5, you'll notice performance degradation. You can take an existing config file and modify it or use the program Gen-conf to create one. Try to keep minimum amount of comments in the file. Note, the block 4 only contains IP addresses, IP address and netmask or wild carded IP addresses. Never use host names in this block, they will be ignored. Netmasks can be used to get a finer control to ignore a very specific range of hosts. Read the section How to use netmasks at Block 4 if you have specific need to ignore a range of hosts. Otherwise, use wild card and be happy. The block 5 contains all the names and IP addresses of the hosts allowed to execute the counter remotely or locally. The name nd IP of the host running the web server must be at this block.
How to use netmasks at Block 4
This section of the document and the code to use netmasks is written by Davorin Bengez, (dbengez@znanost.hr)1. Summary of changes
`Host ignore' block contains one or more lines with IP addresses of hosts that will be ignored for counter updates.
New feature in this release is possibility to mask off groups of hosts (subnetworks) defined by corresponding network / netmask pairs. This can be useful if we wish to exclude accesses from the hosts on our campus or hosts of people developing the pages.
To accomplish this, each line in host ignore block can take two arguments. If second argument is present, first is assumed to be network address and second the netmask. If only one argument is present, it is taken as a host address or a host address with wild card.
If this concept with "network address / netmask" sound unfamiliar, you should consult your friendly network administrator.
2. How to determine ignore hosts parameters
To configure `ignore hosts' block in configuration file, you should know at least how network / netmask concept works. Here is a brief description.
2.1. IP Addresses and netmasks concept
IP address is a 32 bit value (four octets) that is for readability purposes written as four decimal values separated by a dot (so called dotted quad). For example, network address - in dotted quad notation
161.53.4.28is - in binary notation10100001 00110101 00000100 00011100Binary representation is what we will need to determine network addresses and netmasks.Each network IP address is contained of network and host part.
Generally speaking, networks are split into several classes. Here are three primary forms [1]:
- class A network has first octet in range from 0 to 127. First octet is network address while other three octets specify the host part. In binary notation it is something as (n - network, h - host)
0nnnnnnn hhhhhhhh hhhhhhhh hhhhhhhhThere are 27 such possible networks, each with (224 - 2) hosts.- class B network has first octet in range from 128 to 191. First two octets are the network address, and third and fourth are host address. In binary notation it is something as (n - network, h - host)
10nnnnnn nnnnnnnn hhhhhhhh hhhhhhhhThere are 214 such possible networks, each with (216 - 2) hosts.- class C network has first octet in range from 192 to 223. First three octets are the network address, and fourth is host address. In binary notation it is something as (n - network, h - host)
110nnnnn nnnnnnnn nnnnnnnn hhhhhhhhThere are 221 such possible networks, each with (28 - 2) hosts.Note: "-2" is because 0 is reserved for "this host", and 255 means broadcast, or "all hosts on this network".
Nothing stops us to divide the network given to us by a service provider into a several smaller networks. This is often done in real life.
Network is being partitioned by setting the 32-bit subnet mask in which 1's represent the network part, and 0's represent the host part if IP address. As of now, we may correctly assume that a default netmask for class B network is 11111111 11111111 00000000 00000000 (in binary, or 255.255.0.0 in dotted quad notation).
For example, if we are given one class C network (maximum of 254 hosts), and we want to partition it into 8 networks of 32 hosts per each subnetwork, we can do it as in the following example:
Example:
Let us assume that we are given class C network with address 220.105.101.0. Initial netmask is set to 255.255.255.0. To partition this network into 8 subnetworks, we need to take 3 bits from host part of the address (23 = 8). Let's write it in binary:
Network address 220.105.101.0:
11011100 01101001 01100101 00000000Netmask was 255.255.255.0:11111111 11111111 11111111 00000000As we want to have 8 subnetworks (this needs 3 bits from the host part), netmask will be: 11111111 11111111 11111111 11100000 or 255.255.255.224 in dotted quad notation.Host part of address has shrunk to 5 bits, and we will have new network address based on 25 intervals. Therefore, our new subnetworks will be:
220.105.101.0 220.105.101.32 220.105.101.64 220.105.101.96 220.105.101.128 220.105.101.160 220.105.101.192 220.105.101.224n.b. The same netmask (255.255.255.224) applies to each of the 8 networks.From previous example can be seen that netmask cannot be set on arbitrary boundary, but rather on addresses that are powers of 2.
2.2. Configuration guidelines
As a matter of fact, it doesn't matter whether your network is class A, B or C. What matters is which subnetwork or part of the network you want to mask off.
To determine whether a certain host is within a certain network, the host's address AND netmask is compared to the network address. If they are identical, host is within the given network.
Example 1: Determine whether host 161.53.4.4 is located within the network 161.53.4.0 with netmask 255.255.255.0:
since 161.53.4.0 = 161.53.4.0, host is contained within the network.
decimal binary host address 161.53.4.4 10100001 00110101 00000100 00000100 netmask 255.255.255.0 11111111 11111111 11111111 00000000 ANDed 161.53.4.0 10100001 00110101 00000100 00000000 network address 161.53.4.0 10100001 00110101 00000100 00000000Example 2:
Determine whether the host 161.53.91.7 is located within the network 161.53.91.0 with netmask set to 255.255.255.224
since 161.53.91.0 = 161.53.91.0, host is located within the network.
decimal binary host address 161.53.91.7 10100001 00110101 01011011 00000111 netmask 255.255.255.224 11111111 11111111 11111111 11100000 ANDed 161.53.91.0 10100001 00110101 01011011 00000000 network address 161.53.91.0 10100001 00110101 01011011 00000000Example 3:
Determine whether the host 161.53.91.99 is located within the network 161.53.91.0 with netmask set to 255.255.255.224
since 161.53.91.96 != 161.53.91.0, host is NOT located within the network.
decimal binary host address 161.53.91.99 10100001 00110101 01011011 01100011 netmask 255.255.255.224 11111111 11111111 11111111 11100000 ANDed 161.53.91.96 10100001 00110101 01011011 01100000 network address 161.53.91.0 10100001 00110101 01011011 00000000To set the netmask properly, and to check the configuration, you must know what addresses are being covered with certain network address / netmask combination.
Example 4:
Which host are located within the network 161.53.91.0 with netmask set to 255.255.255.224?
It is obvious that only last 5 bits are host address, since netmask will mask off upper 3 bits in last octet. Possible host addresses are from 0 (which cannot be used) up to 00011111 binary, or 31 in decimal. Therefore, hosts within given network are 161.53.91.1 to 161.53.91.31. (n.b. with above configuration, we have possible networks:
decimal binary network address 161.53.91.0 10100001 00110101 01011011 00000000 netmask 255.255.255.224 11111111 11111111 11111111 11100000
Example 5:
How can I select hosts with addresses in range 161.53.5.16 to 161.53.5.31?
It can be observed that host part is last four bits of the address, which leads to the netmask of 255.255.255.240. Network address is address of any of the hosts ANDed with netmask:
References:
[1] Douglas E. Comer "Internetworking With TCP/IP - Principles, Protocols, and Architecture" [2] Uyless Black "TCP/IP and Related Protocols"
Count will try to return an image in any event. That is, even if it fails for some reason, it will write the error messages in GIF format. The text error messages also will be written to the counter log file defined with LogFile in the directory defined with LogDir in the config.h file. The program Count-config asked about these if you remember.If you see any of these images, please check the Counter log file you defined with LogDir and LogFile. If the program could not create the log file, it will write the error messages to stderr. In that case if you configured your httpd server to write the log to a file, the error messages will the written to this file.
1. My CGI scripts don't work. What's wrong?
Answer: Simply linking from your page to an executable program or script won't cause it to be run by the server. There are two common arrangements: either files in directories specially designated by the server administrator are executed as CGI scripts, or files with a special extension (such as .cgi) are executed as CGI scripts.These are just two possible ways your server might be configured. Many sites don't allow users to run CGI scripts at all. Consult your web server's administrator.
Taken from WWW FAQ
2.I get errors while compiling on SGI, what's the problem?Answer: In SGI you might get errors like:: libCombine.a : - Too many arguments *** Error code 1 (bu21) *** Error code 1 (bu21)To make it work, in combine/Makefile, remove the line$(RANLIB) $@Thanks to avarro@CENTRCN.UMontreal.CA (12/07/95)
3. Why does the counter show "888888" all the time?Answer:The counter is running in strict mode (look at count.cfg file). When the counter runs in strict mode, if the browser does not return the environment variable HTTP_REFERER, the counter will display the image 888888 instead of serving the counter. The environment variable HTTP_REFERER should contain the web page running the counter. Some browsers does not return this variable in <img GET method. This feature guarantees that the counter can not be accessed remotely to mess up the datafile from a browser like yours. Some entries in the log file are made including the browser type.
4. The counter does not compile on UnixWare with cc, why?Note for UnixWare 2: Before running the configure script, set and export the environment variable CC to the stringcc -XcThanks to Ed Horch, ebh@fpk.hp.com
5. The counter does not compile on Solaris with cc, why?If you are using Sun's cc on Solaris, you may get errors about identifier redeclaration. Remove the line#include <unistd.h>from count.h. Recompile. You will get some errors about undefined variables. Look at/usr/include/unistd.hand add those defines incount.h. recompile.
6. I get an error message "Could not write to counter file: x/y/sample.dat". What's the problem?Answer: That means the user running the web server can not write to the datafile. The correct way to make it work is to change the owner of the datafile to the user running the web server and give read/write permission to that user only. You can only do that if you're the super user. If you are not super use, you have to give read/write permission to that world. In Unix, "chmod 666 file" will do that. But this will allow anyone to edit or delete your datafile.
7. What does it mean when you say "user running the web server"?Answer: Web servers can be configured to run the CGI program as a unique user and a group. In apache web server, the user and the group is specified with the directive User and Group in httpd.conf file respectively. I suggest create a unique user and group first. For the user, put a * in the password field in passwd file and use /bin/true as its shell. This way this user will never be able to login to the system. And all CGI programs should be owned by the user and read/write/execute permission to be given to that user only. Most of all, make sure you look at all the CGI programs in your system. CGI programs are always a security risk. But if you configured your server to execute CGI programs as a unique non-privileged user, the damage to your system will be minimal, in case security is compromised due to CGI programs.
8. The counter seems to display random number. What's the problem?Answer: If you do not specify a datafile with df= parameter, the counter will display a random number.
9. I get an error message "Host foo.com is not authorized". What's the problem?Answer: Find the file count.cfg. Edit it your favorite text editor. Add the hostname in the error message at block 5. If you do not have access to the file, you have to ask the person who installed the counter.
10. What's the format of the data file?Answer: The counter data file is a text file. The format of this file is:digits:IP Example: 5678765456723456787567876567856:131.349.3.10The digits are the numeric ASCII characters and IP is the IP number of the last host visited the page.
11. How can I reset the counter?Answer: To reset the counter, find the file specified with df= parameter, edit it with your favorite text editor. If you do not have access to the datafile, your sysadmin has to do it for you.
12. How this program handles remote execution?Answer: If you do not know, in most cases any CGI program can be executed remotely without visiting the page with a browser. For example, a CGI program x.cgi (say it returns an in-lined image) in foo. com can be called from foobar.com as follows:<img src="http://foo.com/cgi-bin/x.cgi">That is, someone somewhere on the Internet can refer to your counter and increase the hits and you will not have a clue. You will get the false impression of many people visiting your page.So how this program handles this? The counter program tries to get a environment variable called HTTP_REFERER for remote referrer. It is necessary to check this variable because when someone remotely refer to a CGI program to your machine, the variable REMOTE_ADDR will be the address of your machine. So checking REMOTE_ADDR will not work. Most of the modern browsers returns the env variable HTTP_REFERER. If the browser does not return the variable, counter will be served anyway. But you are not lost totally here. If you decided to ignore count for your host running httpd, the counter will be served but it will not be increased. So, I suggest ignore count for your own host. Gen-conf program is used for generating the configuration file.
Note this is a simple solution of a complex problem. Due to the architecture of the web itself, a determined evil hacker can always circumvent it.
13. What's the maximum number of hits the counter can handle?Answer: By default compile time option, it can handle digits up to 80 character long. However, this can be easily increased by editing the MAX_DIGITS directive in count.h. Now a pop quiz, if a site gets one million hits/day, in which year the counter will get hosed?
14. I sent you so many mails, how come you never respond?Answer: I receive enormous number of mails. Please understand that no way I can answer all of the mails I receive. If the problem can be solved by reading the documentation, you won't hear from me, otherwise I try my best to respond. But often I just have too much to do and mails pile up. If you do not hear from me in 3 days, please send the mail again but please note, your question should not be "please tell me how to install the program".
15. How can I turn off "Reload Ignore" feature?Answer: Edit Makefile with your favorite text editor and uncomemnt the line#COUNT_RELOAD= -DCOUNT_RELOAD=1. That is, remove the # from the beginning. Then recompile, reinstall.
Copyright 1995-1997 by Muhammad A Muquit. Permission to use, copy, modify and distribute this program is hereby granted without fee, provided that this copyright notice appear in all copies and that both that copyright notice and this permission notice appear in supporting documentation. If the program is included in a book, publication or in a software distribution media for sale, the author must be notified about it. If source is modified or enhanced and used in a public site, the source code must be made public on request and it must be clearly mentioned in the documentation what was modified.THIS PROGRAM IS PROVIDED "AS IS" WITHOUT EXPRESS OR IMPLIED WARRANTY. THE AUTHOR DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL THE AUTHOR Muhammad A. Muquit BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTUOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Note: This program is developed in my own time. My employer has nothing to do with it.
Thanks to John Cristy for ImageMagick. I took many routines from ImageMagick for the GIF image combining library. I borrowed the font array and some code from gd library. Thanks to Tom Boutell. Thanks to Philip A. Nelson (phil@cs.wwu.edu) for writing GNU bc. I took a portion of the library to add two big numbers. Special thanks to Kevin J. Walsh. Without Kevin, the counter won't be in the current stage. Kevin did the major code overhauling in Count version 2.0. Thanks to all of you who showed interest in the counter program. I had fun writing it.
If you are using this program, I like to hear from you. If you are having any problem with the program, please let me know as well. Feel free to send any suggestion. If you think that the program is cool, please consider sending me a picture postcard of the area where you live. Thanks to all of you who sent me the nice postcards. I really appreciate it.Muhammad A Muquit
Fox Chase Cancer Center
Research Computing Services (C119)
7701 Burholme Avenue
Philadelphia, PA 19111
USA
Thanks.
Enjoy!
Count 2.4
Count 2.3
Count 2.2 (January 16, 1996)
Count 2.0 (December 27, 1995)
<img src="/cgi-bin/Count.cgi?df=count.dat">
or as complex as before. or any attribute can be set independently.
Count 2.0b
Thanks to John Anthony Ruchak for beta testing Count 1.5.
Count 1.5 (September 11, 1995, 9:00 PM EDT)
(September 10, 1995)
Count 1.4 (August 27, 1995)
Count 1.3